Encryption at Rest vs. In Transit
TL;DR:
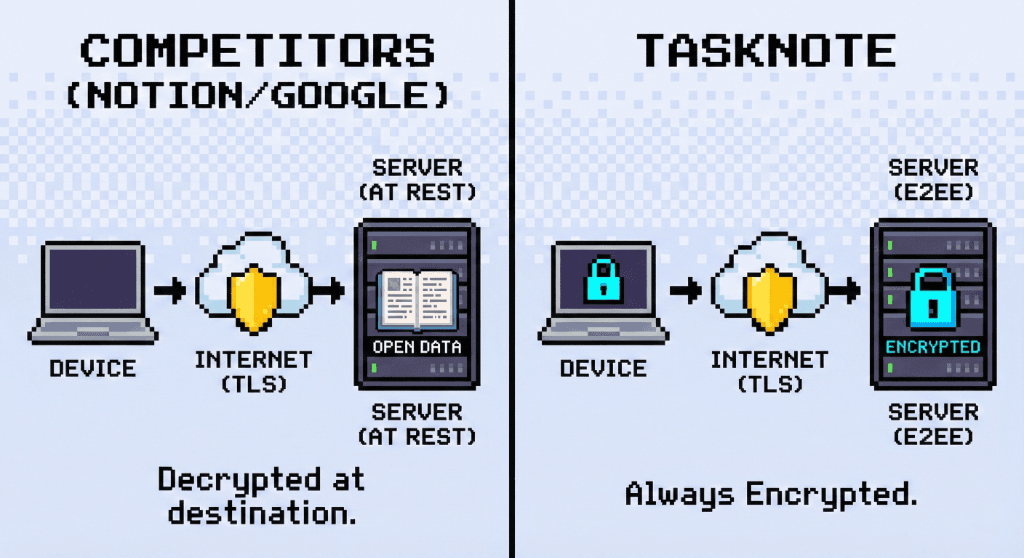
Encryption in Transit protects your data while it travels through the internet (preventing Wi-Fi snooping). Encryption at Rest protects your data while it sits on a hard drive server (preventing physical theft). However, neither of these prevents the service provider (Google, Notion, etc.) from reading your data, because they hold the keys to decrypt it at the destination.
🚚 The Armored Truck Analogy
Imagine you are moving gold bars (your data) to a bank vault (the cloud).
- Encryption in Transit (The Truck): You put the gold in an armored truck to drive it to the bank. Thieves on the highway cannot steal it. This is standard HTTPS/TLS.
- Encryption at Rest (The Vault): The bank puts your gold in a strong steel vault. Thieves breaking into the bank at night cannot steal it.
- The Problem: The bank manager has the key to the vault. He can open it anytime, look at your gold, count it, or hand it over to the police.
TaskNote adds a third layer: You put the gold inside an unbreakable personal box before putting it in the truck. The bank stores your box in their vault, but they (and their manager) cannot open it.
🚦 Encryption in Transit (HTTPS)
This is the green padlock icon you see in your browser URL bar.
- Technology: TLS (Transport Layer Security) or SSL.
- What it stops: It stops a hacker in a coffee shop (Man-in-the-Middle attack) from intercepting your password when you log in.
- Limitation: The encryption ends the moment data reaches the server. The server decrypts it to "read" the request.
🗄️ Encryption at Rest
This means the hard drives on the server are encrypted.
- Technology: AES-256 (usually server-side).
- What it stops: It stops someone who physically steals the hard drive from the data center.
- Limitation: The application running on that server must have the decryption key to function (to index your notes for search, for example). Therefore, the data is accessible to the application and its admins.
🏆 The TaskNote Difference
We use both, but we add the most important layer: Client-Side Encryption.
Because your notes are encrypted before transit and remain encrypted at rest using a key we don't possess:
- In Transit: Even if TLS is broken, the attacker sees only ciphertext.
- At Rest: Even if our database is leaked, the attacker sees only ciphertext.
- In Use: Even our server processes cannot read your notes.
When choosing a note-taking app, don't settle for just "Encryption at Rest." Demand that the keys stay with you.
❓ Frequently Asked Questions (FAQ)
Is "Bank-Grade Security" the same as E2EE?
No. "Bank-Grade" is a marketing term usually referring to AES-256 Encryption at Rest. Banks need to see your transactions to prevent fraud, so they do NOT use End-to-End Encryption for your financial data. For notes, you want E2EE.
Does TaskNote use HTTPS?
Yes. We use strict TLS 1.3 for all connections. This protects metadata (like "User A is syncing") even though the content itself is already encrypted by your client key.
Why is Encryption at Rest not enough?
Because it trusts the storage provider. If a rogue employee at a cloud company decides to read user data, "Encryption at Rest" won't stop them, because the system automatically decrypts data for authorized employees.